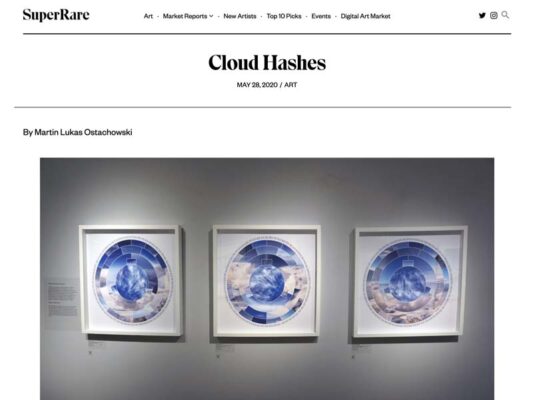
My current body of work explores technical blockchain concepts, which I try to visualize for a broader audience. One of the ideas which stuck with me is hashing and its power to verify the integrity of data securely. It inspired this visualization project entitled Cloud Hashes, which I used to introduce visitors to the process of hashing during my blockchain-themed art exhibition. The artwork itself consists of three animated, tokenized digital artworks; in addition, I created a limited print edition of 5 each.

SHA-256 Background
Since Bitcoin uses the SHA-256 algorithm, my artwork visualizes and references many elements of this hash function. SHA stands for Secure Hash Algorithm and 256 for the number of bits. Designed by the NSA, this SHA-256 algorithm creates a unique fingerprint of any text or file mathematically. This unique fingerprint is called the hash. What makes it secure and desirable is that with the slightest modification of the original text, the output hash is entirely different.
Example 1: “crypto art” results in the following hash:
67DAC4E220E4D161A36FD3E7312B2F7AC3333498CF946CEBE5D48EB6F222AA37
Example 2: “Crypto art” with a capital C leads to the following hash:
69AAE4DC4E666E0EA56EF15AAA6EEC30DF2F6015DF6CB964FCB5E80DB41CA17A
It is just as easy to verify the integrity of vast amounts of data, i.e. the contents of all books ever written, as they can be hashed to the exact same-length output hashes. In the following, I will deconstruct some of my SHA-256 algorithm references.
Cloud Hashes – Deconstructed
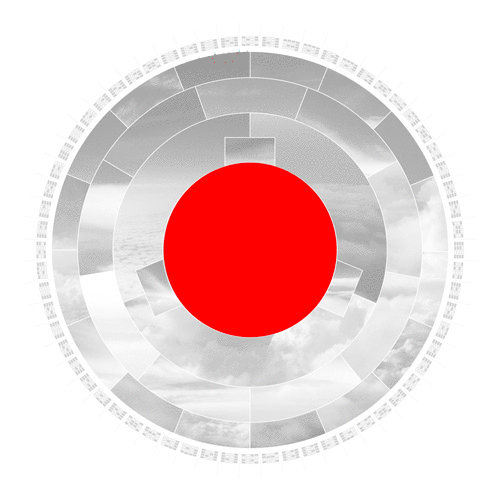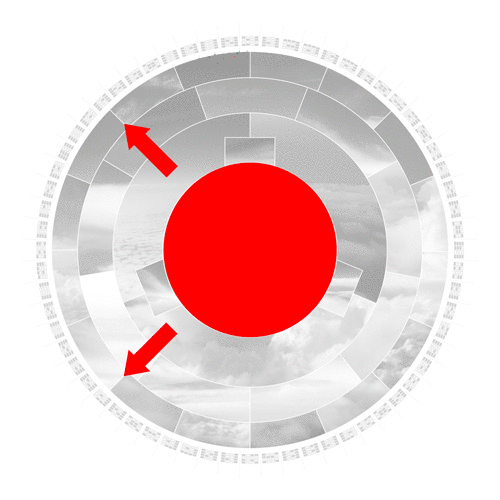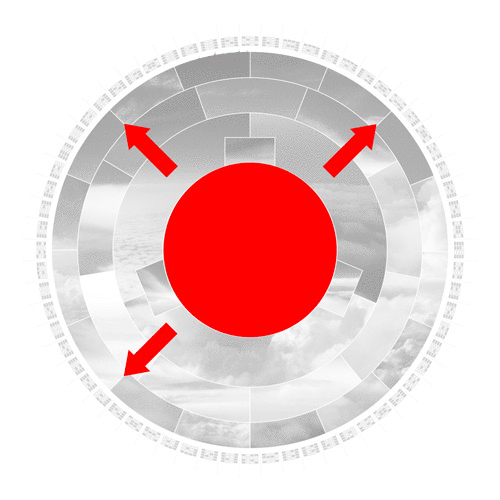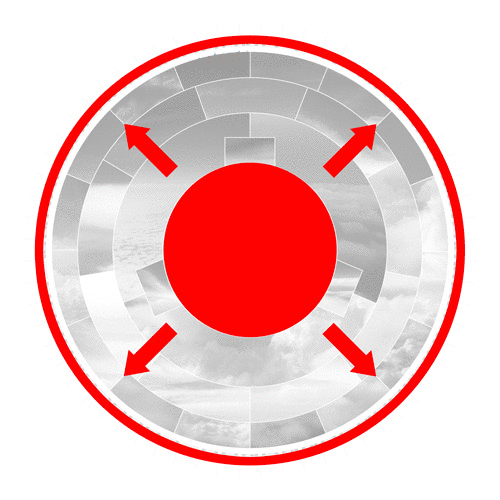
In a nutshell, the center photo represents the input, which leads to the creation of a SHA-256 hash in the outer ring. The rings in between represent the several stages the algorithm works through to convert this input to an output hash.
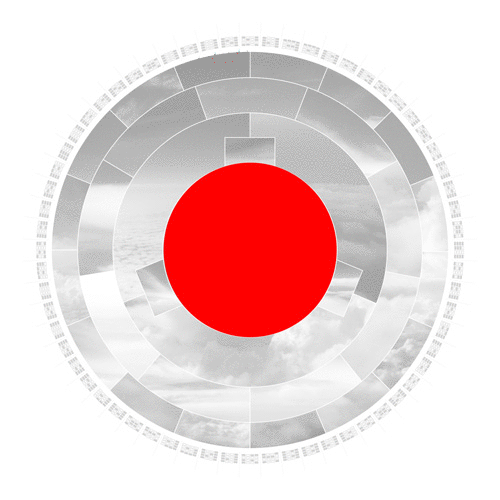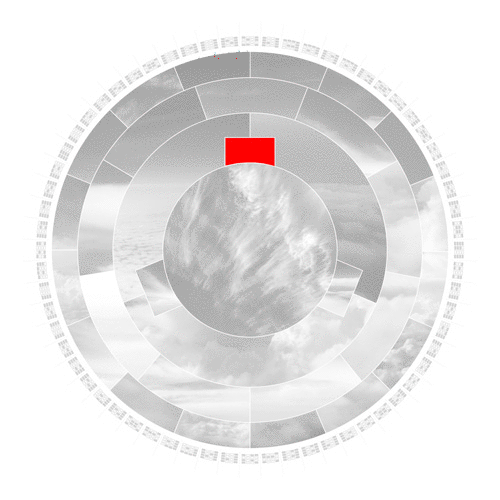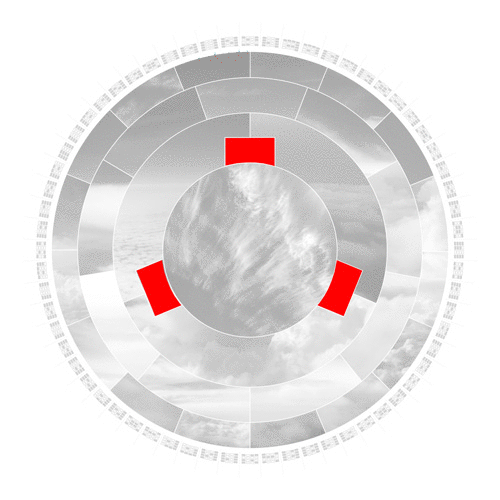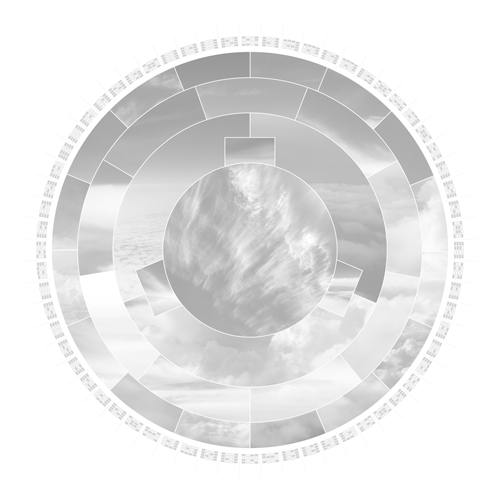
In the first step, the hashing algorithm splits the input image into its fundamental parts.

The algorithm converts the input to binary code and pads it with additional bits to comply with its specified length to operate further.

The compression algorithm then mathematically slices, stretches, shuffles and scatters the data iteratively. Even the slightest change to the initial input image drastically changes the result of each iteration. This desirable effect is called the avalanche effect.

In the last step, the algorithm converts the binary code to base-16, a hexadecimal numeral system. The 16 segments in this ring represent the possible values 0-9 and A to F. The hexadecimal format is the format we humans interact with hashes since it is substantially shorter.
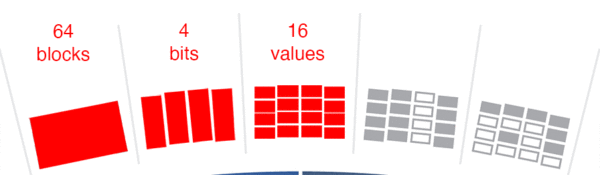
The outer ring shows the real SHA-256 hash. Sixty-four blocks build the 64 alphanumerical characters of the output hash. Each block consists of 4 binary bits, which allow precisely 16 possible values.
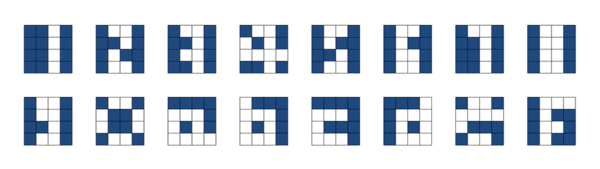
To better visualize the hexadecimal value, I created a readable small-caps font based on this grid of 16.
Tokenized Cloud Hashes
In the animation, the input image in the centers turns in 70 degrees intervals, and the hash algorithm starts subsequently processing through all stages and generates output hashes.
Since the videos would be identical but for their starting point, I have worked with Colorado-based audio engineers Alex Scott and Callum Bair on the creation of three different ambient soundtracks to make the videos as distinct as their hashes.
Tokenized and available on SuperRare
Tokenized and available on SuperRare
Tokenized and available on SuperRare
Cloud Hashes – Limited Print Editions
I created limited print editions of 5 for each of the Cloud Hashes. The three animations mentioned above serve as the respective augmented reality layer for the prints and can be brought to life with the free Artivive app for iOS and Android.

Cloud Hash One
Archival print with augmented reality layer (view with Artivive app)
20 x 20 in. / 50.8 x 50.8 cm
Limited edition of 5

Cloud Hash Two
Archival print with augmented reality layer (view with Artivive app)
20 x 20 in. / 50.8 x 50.8 cm
Limited edition of 5

Cloud Hash Three
Archival print with augmented reality layer (view with Artivive app)
20 x 20 in. / 50.8 x 50.8 cm
Limited edition of 5
Not Nerdy Enough?
Trying to crack the initial message of a hash would currently take even supercomputers years. Hence the best method appears to be guessing, but with 2^256 possible combinations, it is highly unpromising. The number is close to the number of atoms in the known visible universe.
Bitcoin uses two hash algorithms, SHA-256 and RIPEMD-160. One can consider this as a belt and suspender solution.